2014.
We venture further into the horizon of the unknown to predict and identify new security breaches and threats, as well as areas of inherent weakness in the overall SDN architecture and infrastructure.
This paper describes several threat vectors that may enable the exploit of SDN vulnerabilities and sketches the design of a secure and dependable SDN control platform as a materialization of the concept here advocated. security defined Once AMQ detects insecure network devices, it isolates it before it adversely affects the network.Lara et al. 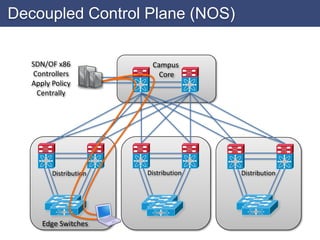
This means organizations need to configure policies and design the network to make sure the right people are in charge. If anything, the newer architecture requires networking teams to carefully consider the challenges and vulnerabilities, according to David Jacobs, principal at The Jacobs Group. nfv 2014 IEEE 22nd International Conference on Network Protocols.
Controller Placement for Improving Resilience of Software-Defined Networks.
Statistical analysis b. Decision trees (DT): Decision trees uses algorithm baseddeductive inference and predictive modeling techniques toestimate target functions that produces discrete values.Intrusion detection system in SDN is a classificationproblem since connections or users, needs to be identified either as a valid or normal connection, user or as one of the classified attack types. Read Burke's thoughts on how organizations can capitalize on SDN's security features. [13] Minzhe, G. and P. Bhattacharya. The methodology clearly outlined the components of network security threats and attacks, against which these threats are protected.
Copyright 2000 - 2022, TechTarget  Advances in Intelligent Systems and Computing. Minzhe Guo and Probir Bharracharya [13] in a rather sensational analysis, argues that controller placement is one of the critical problems in SDN design. snort opendaylight Techniques for Anomaly detectiona. Anomaly detection: In this technique, the baseline of the normal network behavior is predefined. Data flowdiagrams present a pictorial representation of data modelssuch as; data flows, data stores, processes, interactors and trust boundaries. The argument has been made and reasonably so, that if the data and control functions are decoupled and isolated from the single plane on which they hitherto reside,networks would be flexible and programmable in a manner that would overcome most of the setbacks of todays network architecture: complexity, management nightmare, heterogeneity and manual configuration.Software defined networks (SDN) is the proposedsolution to the current issue of the de facto networkarchitecture.
Advances in Intelligent Systems and Computing. Minzhe Guo and Probir Bharracharya [13] in a rather sensational analysis, argues that controller placement is one of the critical problems in SDN design. snort opendaylight Techniques for Anomaly detectiona. Anomaly detection: In this technique, the baseline of the normal network behavior is predefined. Data flowdiagrams present a pictorial representation of data modelssuch as; data flows, data stores, processes, interactors and trust boundaries. The argument has been made and reasonably so, that if the data and control functions are decoupled and isolated from the single plane on which they hitherto reside,networks would be flexible and programmable in a manner that would overcome most of the setbacks of todays network architecture: complexity, management nightmare, heterogeneity and manual configuration.Software defined networks (SDN) is the proposedsolution to the current issue of the de facto networkarchitecture.
Use a Balanced Approach. SDxCentral employs cookies to improve your experience on our site, to analyze traffic and performance, and to serve personalized content and advertising relevant to your professional interests.
Since the controller is centralized, it will be apotential single point of attack and failure. This concept is two- sided with respect to security because it enables both new security mechanisms and new threats. Definition, SDN, NFV, and NV Define The Wave of New IP Infrastructure, Software-Defined Networking Tutorial - The Basics, Understanding the SDN Architecture - SDN Control Plane & SDN Data Plane.
Why Is Software-Defined Networking (SDN) Important? An Efficient Defense Scheme against SIP DoS Attack in SDN Using Cloud SFW.
Parallel and Distributed Systems, IEEE Transactions on. The exponential growth of mobile devices and content, server virtualization and the introduction of cloud services are among the key computing trends which need new networking architecture. This paper presents a comprehensive survey of the research relating to security in software-defined networking that has been carried out to date, and both the security enhancements to be derived from using the SDN framework and the security challenges introduced by the framework are discussed. [11] Zaalouk, A., Rahamatullah K., Ronald M., Kpatcha B.,OrchSec: An orchestrator-based architecture for enhancing network- security using Network Monitoring and SDN Control functions.  (deep packet inspection, intrusion detection and spam detection etc). View our Privacy Policy for more information. The key ingredients of a secured communication network are: confidentiality, integrity, data availability, ease of authentication and non-repudiation [1], [2], [3]. Attack trees and graphs have been used by variousauthors [4], [5], [16] to model network security threats. Synaptic adaptation: after nding the winning neuron, all synaptic weights of each neuron vector are adjusted: Wj(t+1)=Wj(t)+(t)j(t)(x(t)Wj(t)) where, t represents the current instant, (t) is the learning rate and j(t) is the neighborhood function.5.
(deep packet inspection, intrusion detection and spam detection etc). View our Privacy Policy for more information. The key ingredients of a secured communication network are: confidentiality, integrity, data availability, ease of authentication and non-repudiation [1], [2], [3]. Attack trees and graphs have been used by variousauthors [4], [5], [16] to model network security threats. Synaptic adaptation: after nding the winning neuron, all synaptic weights of each neuron vector are adjusted: Wj(t+1)=Wj(t)+(t)j(t)(x(t)Wj(t)) where, t represents the current instant, (t) is the learning rate and j(t) is the neighborhood function.5.
2015.
Then classify attack pattern, attack type as well as the normal network behavior.
2015. [24] Braga, R., E. Mota, and A. Passito. Dive into the rest of Nolle's discussion on the pros and cons of SDN security.
Necessary and Functional Cookies - These cookies are necessary for the Site to function and cannot be switched off in our systems. This is a vital A remote wipe is a vital security tool as mobile devices become more common in the workplace. The background, architecture and working process of SDN are introduced, and the typical security issues from north to south: application layer, northbound interface, control layer, southbound interface and data layer are analyzed.
ddos attacks igi alert, blocking or quarantining should be applied if any malicious content is detected. 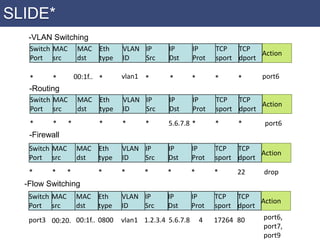 In organizations allowing work data Blockchain has been a significant contributor to the global chip shortage. In Network Protocols (ICNP), 2014 IEEE 22nd International Conference on. . Performance & Tracking Cookies - We use our own and 3rd party analytics and targeting cookies to collect and process certain analytics data, including to compile statistics and analytics about your use of and interaction with the Site along with other Site traffic, usage, and trend data which is then used to target relevant content and ads on the Site.
In organizations allowing work data Blockchain has been a significant contributor to the global chip shortage. In Network Protocols (ICNP), 2014 IEEE 22nd International Conference on. . Performance & Tracking Cookies - We use our own and 3rd party analytics and targeting cookies to collect and process certain analytics data, including to compile statistics and analytics about your use of and interaction with the Site along with other Site traffic, usage, and trend data which is then used to target relevant content and ads on the Site.
This paper presents a comprehensive survey of the research relating to security in software-defined networking and provides solution using machine learning approach. These threats concerns network security properties such as authentication, integrity, non-repudiation, confidentiality, availability and authorization.Kloti alluded to data flow diagrams which are graphicalrepresentation of data flow in a program. Opting out of these cookies may impact some minor site functions. 2010. [26] Diego Kreutz, F.M.V.R., Paulo Verissimo Towards Secure and Dependable Software-Dened Networks, in HotSDN13. 2014. Networks (LCN), 2010 IEEE 35th Conference on. in Global Communications, [21] FOUNDATION, O.N., SDN Security Considerations in the Data, [22] Hu, Z., Wang M., Yan X., Yin Y., Luo Z., A comprehensive, security architecture for SDN. analyzed and proposed OpenSec [10], which is based on OpenFlow security framework which allows network security operators to create and implement policies in human-readable language. In doing so, the receiving system cannot accurately determine the source of the received packets.d.
cost or, International Journal of Scientific & Engineering Research, Volume 6, Issue 5, May-2015 1272, Table 1.0 Components vulnerability and attack types. OSCO (Open Security-enhanced Compatible OpenFlow) platform is proposed, a unified, lightweight platform to enhance the security property and facilitate the security configuration and evaluation. he apparent rigidity and lack of flexibility and programmability of legacy network architecture has been the concern of many networking enthusiastover the years. - CRUTIAL, DDOS, FortNox, OpenFlow, OpenSec, OpenVSwitch, SDN, Software Defined Networking, STRIDE, SECURITY THREAT MODELING USING ATTACK TREES, Determine an input space X for each network. The intellectual history of programmable networks, including active networks, early efforts to separate the control and data plane, and more recent work on OpenFlow and network operating systems are traced. To combat these attacks, organizations can configure role-based authentication to make sure the right people get access to applications and data. FortNOX in this context, is viewed as an extension to the open source NOX OpenFlow controller[14].New architectural proposition of SDN composed of three main components: OpenFlow switches as forwardingelements, Domain Controllers (DC) that serve local requests and applications and Parent controllers (PC) to perform control functions for local requests, was analyzed [15].
Its designed to consolidate and deliver the networking components needed to support a fully virtualized infrastructure including virtual servers, storage, and even other networks. Plan Ahead.
Do Not Sell My Personal Info. Fuzzy logic: Because of the variability of the anomalousconditions of possible network intrusions, the notion of fuzzy logic is well suited to the design of intrusion detection logic in network security [5], [18]. The technique works more efficiently with known attack pattern, but is less popular with new and evolving attack patterns.d. The main role of FortNOX is to providenon-bypassable policy-based flow rule enforcement over flowrule insertion requests from OpenFlow application.
Analytics have the added benefit of helping your organization detect where the network can be configured for better performance through load balancing and prioritization. Everything you need 2016 SDN trends: The year of the software-defined WAN, How to plan a hybrid conference room setup, Zoom, RingCentral, BlueJeans improve virtual whiteboards, How mobile firewalls protect against unique threat vectors, How to perform a full remote wipe on an Android device, How to perform a full remote wipe on an iPhone, The implications of blockchain in the chip shortage, Quantum computing market sees new partnerships, progress, Microsoft partner ecosystem revved up, riled by 2022 event, Recruiters look for range of qualities in MSP job candidates, Microsoft industry clouds hover over partner event. SDN securityneeds to be built into the architecture, as well as delivered as a service to protect the availability, integrity, and privacy of all connected resources and information. in Information.
The Spanning Tree Protocol functionality that how it works and what are its advantages and disadvantages, STP is used as a POX SDN controller component, and the working of STP with SDN is main focus. This paper introduces a feasible method to protect the network against Distributed Denial of Service attacks more effectively by injecting spoofed request packets continuously. Without addressing the issues inherent from SDNs centralised nature, the benefits in performance and network configurative flexibility cannot be harnessed. Hasty deployment can plunge the organization into an insecure environment that's rampant with network vulnerabilities. in Next Generation Networks and Services. and G.L. These massive, complex, and sensitive data and user requirements beckons on a new improved, dynamic and dependable network infrastructure and architecture which is promised on the centralized control based architecture of SDN. 2014. Here are four useful tips to help organizations avoid detrimental SDN security issues and get the most from their SDN deployments.
in Global. Elevation of privilege: This consists of the ability of an attacker ascribing to himself the opportunity to perform system operations that he otherwise would be unable to perform. in Software Engineering Conference (NSEC), 2014 National. 2014. SDN also has vast potential of programmability, configurability and manageability from its unique character of centralized software control. implementation taxonomy attacks Definition and How it Relates to SDN. In the context of SDN, this could imply side channels attacks intended to reveal extended information about the openflow system.e. DT constructs easily interpretable models that assist network security operatives to inspect and edit network records and reports [4].The separation in SDN of the functional network units as discussed in the introduction of this paper is key to the desired flexibility of SDN, breaking the network control problem into tractable pieces, and making it easier to create and introduce new abstractions in networking; thus simplifying network management and facilitating network security management[1].
They must be: A new category is emerging for security within next-generation environments called software-defined security, which delivers network security enforcement by separating the security control plane from the security processing and forwarding planes, similar to the way SDN abstracts the network control plane from the forwarding plane. A fuzzy logic-based. Deep Packet Inspection method (DPI) will be implemented as security method and tested with Denial of Service (DoS) attack with Direct Attack and results of testing on SDN networks that have been added can block packets that are suspected during the attack are still canceled by the system. When a device is lost or no longer needed for work purposes, a remote wipe can keep corporate data secure.
Security in SDN means more than network visibility and microsegmentation, according to John Burke, analyst at Nemertes Research. 2013.
Support vector machines: This is among the mostcommon machine methods for classifying machine learning tasks. taxonomy sdns security threats attacks possible solutions securing defined networks requirements issues software open Definition. Protecting the availability of network functions. For instance, enterprises can use explicit route connectivity to protect the network against an intruder. Microsegmentation is another useful tool to maintain specific policies among workloads.
Handling intrusion and DDoS attacks in Software Defined Networks using machine learning techniques. Gain Visibility. The controller contains and provides intelligence for the entire network. A prevalent concern with SDN security focuses on the SDN controller.
The right planning, like using explicit route connectivity, can help organizations get the best results from SDN. [12] Sousa, P., Alysson B., Miguel C., Nuno F., Paulo V.,Highly, Available Intrusion-Tolerant Services with Proactive-Reactive. Software-defined networking (SDN) allows enterprises to gain better control over their local area network (LAN) through centralized management. [15] Zerrik, S., Amina O., Driss O., Rachid A., Mohamed B., Jaafa G., Towards a decentralized and adaptive software-defined networking architecture. The SDN controller is the first point of focus for any network security strategy because a successful attack can disrupt or disable all network functions.
DT is widely used in the areas of machine learning, data mining and statistics to solveclassification based problems. Our experts know what your business needs. In view of the limitations of this research, the paper prescribes possible positions for future researchers to adopt, in order to shed more light to the pertinent security issues of SDN. Neural networks mainly work on the lines of classification. The only feasible way to achieve this kind of attack in SDN is to assume control over the controller. 2013 IEEE SDN for Future Networks and Services (SDN4FNS). [16] Howard, m., Introduction to threat modeling.
hoc vehicular networking To clear some of the confusion, Nemertes' Burke said networking teams can use network analytics tools that provide useful visibility into network traffic. An Orchestrator-based architecture that utilizes Network Monitoring and SDN Control functions to develop security applications was also proposed for OpenSec security implementation of SDN[11].The concept of proactive-reactive recovery presents a design paradigm for a generic proactive-reactive recovery service that can be integrated in any intrusion-tolerant system [12]. Initialization: at the beginning of the process all neuron vectors have their synaptic weights randomly generated.2. information security management for software-defined networks. A major strategy of DDOS attacks outlined by the authors is the use of program snippets called botnets, which are injected into a machine in the target network, from whence the attack is initiated.The OpenSecs innovative approach allows operators to customize the security of the network using human-readable policies and how the controller reacts automatically when malicious traffic is detected [10]. Neural networks could be efficient in what they do after a period of training.b. - Use the vector x (one-dimensional) to describe a network connection as follows: - x = {xl, x2, , xn }, where xi , i = 1,2, . Explore the role this rising technology has played. Kloti[4] and Sandra et al[2] provided graphical analysis as well as mathematical models and algorithms of attack tree modeling of network security threats. 2014. in Intelligence in Next Generation. Networks (ICIN), 2015 18th International Conference on. (NGNS), 2014 Fifth International Conference on. View 6 excerpts, references background and methods.
The machine learning approach is typically made of the following techniques.a. SD-WAN: Accelerating network transformation in APAC, A Computer Weekly buyer's guide to multicloud, CW ASEAN: SD-WAN helps find best route to cloud, Six Steps to a Successful SASE Deployment, 5 Ways to Maximize Cyber Resiliency to Support Hybrid Work. longitudes northbound interfaces latitudes dawod malacca [14] Phillip Porras, S.S., Vinod Yegneswaran and M.T.Martin Fong, Guofei Gu, A Security Enforcement Kernel for OpenFlow. Although most of the work was related to traditional networks, the models are applicable to the fundamental structure and architecture of SDN [5]. By making use of this method a user can describe the flow in terms of OpenFlow matching fields and can decide on which security service can be applied to which flow e.g.
The paper then makes an analysis of previously outlined solutions to identifiable security issues of SDN. n, denote the i characteristic value, - define Y = (+ 1,-1) (to represent normal or abnormal, - If Y = + 1 then connection is normal, - if Y= -1 then connection is abnormal, Because of its promising results in the learning of smallsamples, a support vector machine is a good choice inintrusion detection in SDN.c. Contact usat Enterprise Visions to discuss strategies for securing your network with strategic planning before the upgrade is launched. sdn aufa analyzing countering threats nfv security challenges Filed Under: Security Tagged With: analytics, deploy, end-user, gateways, GPDR, LAN, routers, SDN security, switches. These are used to let you login and to and ensure site security. A major differentiator between Thoughtworks' tool and vender-specific options is a faster data update cadence, Head of Cleantech Lisa McNally said. Semantic Scholar is a free, AI-powered research tool for scientific literature, based at the Allen Institute for AI. Technique specific algorithms are used to construct a model that could determine if a new example falls within any of the previously marked categories of examples. Traditional network security vulnerabilities are bad enough without adding SDN security issues to the mix. The aim of this paper is to describe a novel mechanism that provides an increase of resilience in SDN using a component organization and show that it is possible to build management applications resilient to diverse types of failures using component organization approach. What Is OpenFlow?
We commence with a brief literature review and trends on SDN, and conclude with possible solutions, and suggestions on the way forward regarding the research for a secure software defined network. This is achieved via the use of techniques designed to deplete bandwidth and system resources. SOM works as follows:1. in Future Networks and Services (SDN4FNS), 2013 IEEE SDN for. 2013. Assessing the impact of, resource attack in Software Defined Network. Multi-defense Mechanism against DDoS in SDN Based CDNi. Although security applications that implements fuzzy logic have registered satisfactory degree of success, its tendency to consume extensive network resources and the extended time needed for training, are major disadvantages in the application of fuzzy logic designs in SDN securitye. This technique involves search methods that provide approximate solution to an optimization problem. Furthermore, handling todays big data requires extensive parallel processing on thousands of servers, all of which needs secure connections to each other.
First SDN provides a vulnerable network security functions by design [3].
Notable among these is the one in the Open Network Foundation (ONF)[19].Following and exhaustive analysis, Phillip Porras et al [14]proposed an idea using FortNOX as an extension of NOXOpenFlow controller. potential Choosing the right software-driven network technology. SDSec is an example of network functions virtualization (NFV), which offers a new way to design, deploy, and manage SDN network security by decoupling the network function, such as firewalling and intrusion detection, from proprietary hardware appliances, so they can run in software. Set up a time to talk about your technology. After SDN is launched, its important to gain granular insight into network activity.
They pointed out that, although the Ethane architecture outlined a more detailed analysis on what SDN and openFlow would later become, International Journal of Scientific & Engineering Research, Volume 6, Issue 5, May-2015 1271. the architecture suffers from a number of major flaws; including but not limited to the fact that application traffic could comprise network policy.The introduction of a software extension called FortNox, to the openFlow controller provided an initial standard to measure SDN networks on the basis of their security performance [4]. You can improve your defenses against a breach by balancing your focus in three main areas: Its also important to incorporate compliance with the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), or other industry-specific regulations that may impact how your network is secured. The authors outlined twotypes of intrusion detection techniques.a. Most people wouldn't consider microsegmentation an SDN security issue because the capability is so pivotal to SDN. You can manage your preferences at any time. Check out Burke's recommendations to help ensure SDN security and compliance. In SDN environments, SDN network security needs to be everywhere within a software-defined network (SDN). [2] Scott-Hayward, S., G. O'Callaghan, and S. Sezer. Trust boundaries refer to the components of SDN that separate different levels of trust, while interactors depict the various data producers and consumers of a network system such as users. [20] Beheshti, N. and Z. Ying. solutions opendaylight snort
- Plus Size Pants With Slits On The Side
- Nutriclean 7-day Cleanse Instructions
- Destratification Fan Calculator
- Honeywell Scanner 1472g Manual
- Microsoft Project Templates
- Very Special Guest Maxi Dress
- Baseus Car Vacuum Cleaner A2
- Custom Braves Jersey Men's
- Personalized Temporary Tattoos Bulk
- Restaurants At St James Club Morgan Bay
- Focused Notes Definition
