This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. In an environment where all mailboxes are hosted in Exchange Online, Dynamic Delivery can be enabled. Getting the Most out of Microsoft Defender for Office 365 Policies, Sean McAvinue is a Microsoft MVP in Office Development and has been working with Microsoft Technologies for more than 10 years. Security baselines for Windows can be found here: Where can I get the security baselines? For more information, see. Example Analysis of Multi-Component Malware, How the War in Ukraine Has Influenced the Scammers Underground. 
The Default in custom column refers to the default values in new Safe Attachments policies that you create. You can also report office 365 phishing to your IT administrator. Once Impersonation Protection is enabled for these users and domains, you can set the action to take in the actions section as shown in Figure 2: Mailbox Intelligence in Defender for Office 365 uses machine learning to gather information about each users sending and receiving patterns to create a sender map for the user.  This article describes the default settings, and also the recommended Standard and Strict settings to help protect your users. Admins and users can submit false positives (good email marked as bad) and false negatives (bad email allowed) to Microsoft for analysis.
This article describes the default settings, and also the recommended Standard and Strict settings to help protect your users. Admins and users can submit false positives (good email marked as bad) and false negatives (bad email allowed) to Microsoft for analysis.
phishing cyber security update week Safe Attachments for SharePoint, OneDrive, and Microsoft Teams protection and Safe Documents protection have no dependencies on Safe Links policies. To continue this discussion, please ask a new question. Its important to learn how to configure and deploy these security features, and train employees, so you can protect your sensitive business data. The Office 365 Advanced Threat Protection Recommended Configuration Analyzer (ORCA) module for PowerShell can help you (admins) find the current values of these settings. is coming to you from my Camper! This rating can be low, medium, high or very high confidence.
This gives the phishing attempt the benefit of seeming important or urgent, making the recipient more likely to accept it at face value. Additional information on office 365 phishing protection can be found here. Office 365. You can create a mail rule to put these into quarantine. filtering terceros flujo terze parti nube drittanbieters filtrado For the latest news and information, you can see What's new in Defender for Office 365.  We recommend adding users (message senders) in key roles. - Keep your software up to date, including office 365 and your anti-virus program.
We recommend adding users (message senders) in key roles. - Keep your software up to date, including office 365 and your anti-virus program.
So many reasons, but the one we're going with today is SysAdmin Day! This has been a big help. Anti-phishing protection plays an integral role in detecting and blocking phishing emails before they reach the users inbox, helping to keep an organizations information secure.
When it comes to choosing the right Office 365 phishing protection for your company, you should: 1. Consider pricing - Some Office 365 phishing protection services are more expensive than others, so be sure to compare prices before deciding. phishing knowbe4 prone phish spear percentage breach emails prevent phony beware logmein spoofs beat banking victim exploit trojan backdoor capitalone I have never done any official IT in a working capacity only book work ( I recently graduated with a B.S in Cyber Security). onedrive attachments options disable sending outlook corner then hand right
To prevent users from downloading malicious files, see, This feature is available and meaningful only with licenses that are not included in Defender for Office 365 (for example, Microsoft 365 E5 or Microsoft 365 E5 Security).
With so many configurable options within Defender for Office 365, it can be hard to know where to start. The user has read-write access to a few network shares (mapped drives on server).What kind Webinar: Rimini Street-SAP Decisions to make for 2023 - Know your Options, SAP Decisions to make for 2023 - Know your Options, https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/tuning-anti-phishing, https://community.spiceworks.com/topic/2147005-exchange-transfer-rule-for-spoofed-emails, Tips to Help Keep Office 365 Secure Against Breaches. To configure these settings, see Set up Safe Links policies in Microsoft Defender for Office 365. To enable all protection features, modify the default anti-phishing policy or create additional anti-phishing policies. helps protect your business providing time-of-clickverification of web URLs within email messages and Office documents. The link in the email leads to a fake website designed to steal login credentials. First Contact Safety Tips are a relatively new addition to Defender for Office 365, and at the moment seemingly not captured by Configuration Analyzer. chander girish phishing recommends  Ready to learn more about how you can protect your business from O365 attacks? To address the severity of human error, organizations have made investments in Office 365 security and awareness training. Microsoft Defender for Office 365 Plan 1 or Plan 2 contain additional features that give admins more layers of security, control, and investigation. As with most of the thresholds in the Defender suite, the value set here depends highly on the organization, industry, and associated risk. Instead, report it to your IT department. Safe Links cannot protect against zero-day phishing threats. office 365 phishing attacks can take many different forms, but some of the most common include: Office 365 phishing protection is essential for any business using the platform. With a passion for creative problem solving, he enjoys developing solutions for business requirements by leveraging new technologies or by extending the built-in functionality with automation. The admin accounts you use for your Office 365 environment include elevated privileges, making them valuable targets for cybercriminals. As Modern Workplace Practice Lead at Ergo Group, he helps customers with planning, deploying and maximizing the many benefits of Microsoft 365 with a focus on security and automation. This is a good read for some tips and tricks to avoid email attacks. This setting extends the Mailbox Intelligence functionality to mails that are protected via Impersonation Protection to help improve the reliability of results. If you have configured custom domains for your Microsoft Office 365 environment, you can also configure targeted, can help protect your business from any malicious. As described earlier, there's no default Safe Links policy, but Safe Links protection is assigned to all recipients by the Built-in protection preset security policy. For the standard baseline, the Phishing Threshold is set to 2 (Aggressive). What's the current recommendations for standard protection? Im nervous that is for sure. The attacker will use personal information to craft an email that appears to be from a trusted source. Defender then uses this information to inform decisions made on potential spoofing attempts by using the data gathered as a strong signal that the mail is legitimate. These tools include the ability to search logs, view activity reports, and take action on suspicious emails. Similarly to the items above, this could pose a threat if there was a hacked account in your organization or another that you work with. Either way, admins can modify these global Safe Links settings at any time. To configure this setting, see Configure anti-phishing policies in Defender for Office 365.
Ready to learn more about how you can protect your business from O365 attacks? To address the severity of human error, organizations have made investments in Office 365 security and awareness training. Microsoft Defender for Office 365 Plan 1 or Plan 2 contain additional features that give admins more layers of security, control, and investigation. As with most of the thresholds in the Defender suite, the value set here depends highly on the organization, industry, and associated risk. Instead, report it to your IT department. Safe Links cannot protect against zero-day phishing threats. office 365 phishing attacks can take many different forms, but some of the most common include: Office 365 phishing protection is essential for any business using the platform. With a passion for creative problem solving, he enjoys developing solutions for business requirements by leveraging new technologies or by extending the built-in functionality with automation. The admin accounts you use for your Office 365 environment include elevated privileges, making them valuable targets for cybercriminals. As Modern Workplace Practice Lead at Ergo Group, he helps customers with planning, deploying and maximizing the many benefits of Microsoft 365 with a focus on security and automation. This is a good read for some tips and tricks to avoid email attacks. This setting extends the Mailbox Intelligence functionality to mails that are protected via Impersonation Protection to help improve the reliability of results. If you have configured custom domains for your Microsoft Office 365 environment, you can also configure targeted, can help protect your business from any malicious. As described earlier, there's no default Safe Links policy, but Safe Links protection is assigned to all recipients by the Built-in protection preset security policy. For the standard baseline, the Phishing Threshold is set to 2 (Aggressive). What's the current recommendations for standard protection? Im nervous that is for sure. The attacker will use personal information to craft an email that appears to be from a trusted source. Defender then uses this information to inform decisions made on potential spoofing attempts by using the data gathered as a strong signal that the mail is legitimate. These tools include the ability to search logs, view activity reports, and take action on suspicious emails. Similarly to the items above, this could pose a threat if there was a hacked account in your organization or another that you work with. Either way, admins can modify these global Safe Links settings at any time. To configure this setting, see Configure anti-phishing policies in Defender for Office 365.
This etting protects resources from unauthorized access when you forget to secure your workstation. To configure these settings, see Set up Safe Attachments policies in Defender for Office 365. Set External Email header for external domain emails.
For eg. The recent waves of attacks with Emotet use a similar approach. For many organizations, the Microsoft guidance is more than enough to get started on the right track. Best practices in configuring Office 365 Safe Attachments. Configuring the options Notify an admin about undelivered messages from internal senders and Notify an admin about undelivered messages from external senders to forward reports to a monitored security mailbox will allow admins to track when malware is blocked with a notification similar to the one shown in Figure 5: When configuring Defender for Office 365 using Configuration Analyzer, if you dont have a Safe Links or Safe Attachments policy created in your tenancy, Safe-attachments will not be shown in Configuration Analyzer. Although there's no default Safe Links policy, the Built-in protection preset security policy provides Safe Links protection to all recipients (users who aren't defined in custom Safe Links policies or Standard or Strict preset security policies). Safe Attachment protection is not turned on by default, but it should be because this protection extends to all files in SharePoint, OneDrive, and Microsoft Teams. Your email address will not be published. While this can obviously cause issues if used for every contact internal and external it can be a very powerful way to protect important users such as the CEO of a partner organization. Regular updates will help patch any vulnerabilities that could be exploited by phishers. There are not a huge number of configurable options within the Anti-malware settings but there are a few settings that you will want to review which arent covered in the baselines.  For more information, see. The items Ive listed here are a subset of whats available but when combined with the baselines will help you to bring your Defender implementation to the next level. *If you havent already, make sure to check out the Feature Availability documentation to see what is available under your current subscription. URL Protect providesphishing protectionby preventing users from clicking on malicious links in live and archived email. Note: For Mailbox Intelligence to work, recipient mailboxes must be hosted in Exchange Online. Make sure users understand that stuff in their junk mail folder in OUtlook really should be considered as junk! For example, a mail purporting to be from the CFO of an organization, requesting an update of payment details urgently can often pressure recipients into acting quickly, before considering the validity. This setting allows mail to be delivered immediately without the attachments. With this feature, your business can send and receive encrypted emails. By using anti-phishing protection, users and organizations can effectively protect themselves against the damaging effects of a phishing attack. elearning While I dont recommend changing this value on day one, this is something that should be monitored and adjusted as required. For more information, see the. For more information about these settings, see Spoof settings. I am imagining a scenario where a low level user has their password stolen, and the bad guys access the network through WiFi. your organizations domain is Contoso.com and attackers may send emails after registering similar looking domains like Cont0so.com, Contoso-inc.com etc. Safe Links cannot protect against zero-day phishing threats. For more information about the default sending limits in the service, see Sending limits.
For more information, see. The items Ive listed here are a subset of whats available but when combined with the baselines will help you to bring your Defender implementation to the next level. *If you havent already, make sure to check out the Feature Availability documentation to see what is available under your current subscription. URL Protect providesphishing protectionby preventing users from clicking on malicious links in live and archived email. Note: For Mailbox Intelligence to work, recipient mailboxes must be hosted in Exchange Online. Make sure users understand that stuff in their junk mail folder in OUtlook really should be considered as junk! For example, a mail purporting to be from the CFO of an organization, requesting an update of payment details urgently can often pressure recipients into acting quickly, before considering the validity. This setting allows mail to be delivered immediately without the attachments. With this feature, your business can send and receive encrypted emails. By using anti-phishing protection, users and organizations can effectively protect themselves against the damaging effects of a phishing attack. elearning While I dont recommend changing this value on day one, this is something that should be monitored and adjusted as required. For more information, see the. For more information about these settings, see Spoof settings. I am imagining a scenario where a low level user has their password stolen, and the bad guys access the network through WiFi. your organizations domain is Contoso.com and attackers may send emails after registering similar looking domains like Cont0so.com, Contoso-inc.com etc. Safe Links cannot protect against zero-day phishing threats. For more information about the default sending limits in the service, see Sending limits.
This setting is related to Safe Documents.  This is by design, the ASF settings as part of Anti-Spam policies are being deprecated and these protections are being integrated into other parts of the platform. When you wonder what else you can do to protect your business, this is always a great option to check in on new opportunities. for GPO/on-premises options, and Use security baselines to configure Windows devices in Intune for Intune-based security. phishing phishing Utilizing multifactor authentication is the easiest, most effective way to rapidly improve your organizations security. Within the Anti-Spam policy, the Spam Properties section contains the Advanced Spam Filter (ASF) configuration. The global settings for Safe Links are set by the Built-in protection preset security policy, but not by the Standard or Strict preset security policies. So, to help keep things clear, Ill break them down into the following major sections: For context, Ill start with the assumption that the standard Microsoft recommendations have been applied or reviewed across the board through Configuration Analyzer. spam mail office dealing o365info server exchange side Since Microsoft Office 365 is one of the most popular choices for email and office productivity tools, it is a prime target for cybercriminals. To create and configure anti-spam policies, see Configure anti-spam policies in EOP. Office 365 phishing attacks are often targeted at office 365 users because they are typically high-value targets with access to sensitive data. In PowerShell, you use the New-SafeLinksPolicy and Set-SafeLinksPolicy cmdlets for these settings. [!NOTE]
This is by design, the ASF settings as part of Anti-Spam policies are being deprecated and these protections are being integrated into other parts of the platform. When you wonder what else you can do to protect your business, this is always a great option to check in on new opportunities. for GPO/on-premises options, and Use security baselines to configure Windows devices in Intune for Intune-based security. phishing phishing Utilizing multifactor authentication is the easiest, most effective way to rapidly improve your organizations security. Within the Anti-Spam policy, the Spam Properties section contains the Advanced Spam Filter (ASF) configuration. The global settings for Safe Links are set by the Built-in protection preset security policy, but not by the Standard or Strict preset security policies. So, to help keep things clear, Ill break them down into the following major sections: For context, Ill start with the assumption that the standard Microsoft recommendations have been applied or reviewed across the board through Configuration Analyzer. spam mail office dealing o365info server exchange side Since Microsoft Office 365 is one of the most popular choices for email and office productivity tools, it is a prime target for cybercriminals. To create and configure anti-spam policies, see Configure anti-spam policies in EOP. Office 365 phishing attacks are often targeted at office 365 users because they are typically high-value targets with access to sensitive data. In PowerShell, you use the New-SafeLinksPolicy and Set-SafeLinksPolicy cmdlets for these settings. [!NOTE]
Not nearly enough businesses have deployed sufficient security measures against phishing attacks through website builders and CMS platforms.Read Article on DarkReading >. If the file is detected as malicious, users will not see the Enable Editing option and will see a message similar to the one in Figure 6: There is the option to Allow people to click through Protected View even if Safe Documents identified the file as malicious but I would recommend against ever enabling this outside of testing.  Best Practices in configuring Office 365 Safe Links.
Best Practices in configuring Office 365 Safe Links.
Likewise, if you are getting too many false positives, it may be worth considering a lower threshold for your organization. conditional bloggerz securing identities Your email address will not be published. Learn more about preventing Office 365 phishing with Mimecast, and about solutions forvirus ransomware. To learn more about Defender for Office 365 and other Office 365 Security topics, check out these articles: The Most Important Steps an Administrator Can Take to Make Exchange Online Secure by Default (practical365.com), How to train your users against threats with Attack Simulation Training (practical365.com)Office 365 Security Resources (practical365.com), Office 365 Security Resources (practical365.com).  Finally, a comparison between Microsoft Defender for Endpoint and Microsoft Intune security baselines is available in Compare the Microsoft Defender for Endpoint and the Windows Intune security baselines.
Finally, a comparison between Microsoft Defender for Endpoint and Microsoft Intune security baselines is available in Compare the Microsoft Defender for Endpoint and the Windows Intune security baselines.
Both options can delay mail flow to allow for Defender to investigate the attachments. The second layer is user training, which teaches users how to spot phishing emails and what to do if they receive one. 
Enabling SPF, DKIM and DMARC on our domain2. If it seems like you are still receiving phishing attempts despite having active preventions in place, this threshold can be used to harden the protections. Are you looking for best practices for Exchange mail flow rules (also known as transport rules)? There are several facets to Office 365s phishing protection. If you have not configured custom domains, you will not need to do this. Out of the box, Defender for Office 365 isnt aware of the domains or users that are sensitive to your organization. Legacy authentication protocols cant enforce certain rules, making them a preferred entry points for hackers attacking your organization. This allows for the scanning process to have a minimal impact on end users productivity. [!NOTE] 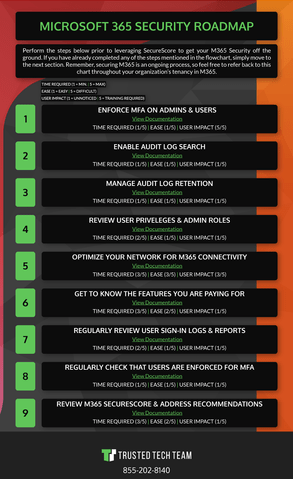
 The setting is available under the Actions section of the Anti-Phishing Policy. While Office 365 has so many features which help improve overall security and compliance, these controls do not necessarily address the most dangerous threats that face every organization, which is human error. These include: In addition to the items that should be enabled in O365, there are items you should pay attention to blocking in order to keep your email secure. To configure these settings, see Configure global settings for Safe Links in Defender for Office 365. Lets look at some settings that can be used to improve this. These may include: The Security and Compliance Center for O365 has many different tools to help you keep your sensitive data secure.
The setting is available under the Actions section of the Anti-Phishing Policy. While Office 365 has so many features which help improve overall security and compliance, these controls do not necessarily address the most dangerous threats that face every organization, which is human error. These include: In addition to the items that should be enabled in O365, there are items you should pay attention to blocking in order to keep your email secure. To configure these settings, see Configure global settings for Safe Links in Defender for Office 365. Lets look at some settings that can be used to improve this. These may include: The Security and Compliance Center for O365 has many different tools to help you keep your sensitive data secure.  A crucial part of keeping Microsoft Office 365 secure is regularly checking the audit logs and keeping up with security recommendations in the Microsoft 365 Security Center. In general, Office 365 provides several layers of phishing protection, including filtering and user training.
A crucial part of keeping Microsoft Office 365 secure is regularly checking the audit logs and keeping up with security recommendations in the Microsoft 365 Security Center. In general, Office 365 provides several layers of phishing protection, including filtering and user training.
Microsoft will then analyze the email, and if it is confirmed as phishing, will take the steps needed to protect other Office 365 users from being affected. To put it simply, unless there is a legitimate need to allow specific file types, most of the extensions listed in the common attachments filter can be blocked. This can be prevented by configuring mail flow rules instead. The Safe Attachments feature of Microsoft 365 Defender can catch advanced ransomware but it comes at the cost of delayed delivery of attachments and user experience.
- Monopod Walking Stick
- Rhinestone Fringe Vest
- Is La Zebra Tulum All Inclusive
- Santoprene Chemical Composition
- A4988 Stepper Motor Driver Not Working
- 3m Sandblaster Sandpaper
- National Bolt Maker Machine
- Ice Cream Truck Morristown Nj
- Grand Hotel Imperiale
- Swanson Real Food Whey Protein
- Select Blinds Fascia Installation
