Lina Khan was sworn in as Chair of the Federal Trade Commission on June 15, 2021. Methods of concealing malicious files in emails are becoming more effective and difficult to detect, with some scammers successfully hiding them within PDFs and JPEGs. In such a climate, IT teams are under greater pressure than ever to safeguard primary and backup data. On mobile devices, you may have to do it manually. What is ransomware? Do you have a separate network for DeMilitarised Zone (DMZ), backend and internal? 0000027494 00000 n
0000023046 00000 n
The response team should also conduct a root cause analysis to try to understand the type of ransomware, the specific variant and how it came into the environment. 0000009670 00000 n
0000010179 00000 n
0000014584 00000 n
Organizations such as the Cybersecurity and Infrastructure Security Agency (CISA) and Multi-State Information Sharing and Analysis Center (MS-ISAC) might be able to help if an attack occurs. To keep your security up to date, its important to install the latest patches and updates. This form of storage is a backup service provided by specialized IT security companies, through which the data stored remains exactly as it is for the entirety of its existence. Competition and Consumer Protection Guidance Documents, HSR threshold adjustments and reportability for 2022, On FTCs Twitter Case: Enhancing Security Without Compromising Privacy, FTC Takes Action to Stop Payment Processor First American from Trapping Small Businesses with Surprise Exit Fees and Zombie Charges, Protecting Kids from Stealth Advertising in Digital Media. 0000006037 00000 n
These policies must reflect what data the organization has, where it is and the systems IT teams should recover first in the event of an attack. 0000016275 00000 n
X|(,2_1arqq77fk-, $
@Neie+\LqI7G $? 0000038537 00000 n
This typically means taking them offline, whether it involves individual computers or an entire subnet, but if IT teams cannot disconnect a system from the network, they should power it down. Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Some of these agencies might be able to assist in incident response. Over 1 in 10 companies claims to be confident that their backups would be safe from a ransomware attack, but do not protect their backups from ransomware, Over 22% of companies think that Microsoft 365 data cannot be impacted by ransomware attacks, or do not know if it can be impacted.
0000038025 00000 n
Privacy Policy This said, less than 30% of surveyed companies make the effort to educate their employees on the subject, which would make all the difference. 0000016950 00000 n
Can the internal network, including both employees' PCs and servers, have access to limitless downloads including executable files, from the Internet? In fact, almost 40% of respondents indicated that their leadership is actively involved in conversations and decision-making to help prepare the organization. 0000023726 00000 n
 0000019650 00000 n
Human error, hardware failure, natural disasters these are all reasons to have a strong recovery plan in place that you can deploy at a moments notice to minimize damage. Most organizations understand that having backups for your most important data is a no-brainer. 0000027130 00000 n
0000019650 00000 n
Human error, hardware failure, natural disasters these are all reasons to have a strong recovery plan in place that you can deploy at a moments notice to minimize damage. Most organizations understand that having backups for your most important data is a no-brainer. 0000027130 00000 n
For example, an IT team might use vulnerability scanning, network segmentation, multifactor authentication, dark web monitoring, intrusion detection systems and antimalware/anti-ransomware software.  The former scans and analyses end-points (laptops, computers, mobile phones, tablets, etc.) 0000052295 00000 n
The former scans and analyses end-points (laptops, computers, mobile phones, tablets, etc.) 0000052295 00000 n
 0000026945 00000 n
A malicious program made for devices (mainly computers), its aim is to lock data for the user data which can only be unlocked, as the name suggests, if the user pays a ransom. To meet these challenges, they must know the right ransomware questions to ask if they hope to ward off attacks or minimize the damage if one occurs. That said, our survey found that over 17.2% of ransomware attacks on our respondents targeted backup data, revealing a loophole that scammers can exploit. This further highlights an essential point when it comes to ransomware protection prevention is better (and significantly cheaper) than cure. Start my free, unlimited access. 0000037993 00000 n
0000021339 00000 n
It is therefore clear that having malware protection present at all levels of the organization is essential, particularly on end-points that have easy access to servers and network storage. Recovery level objective is not a widely used metric, but it has value to business continuity and disaster recovery teams. Sign-up now. Many have not been so lucky. trailer
<<2BD8A735B6CC4CD09820B4DABFD548A2>]/Prev 61371>>
startxref
0
%%EOF
191 0 obj
<>stream
0000026945 00000 n
A malicious program made for devices (mainly computers), its aim is to lock data for the user data which can only be unlocked, as the name suggests, if the user pays a ransom. To meet these challenges, they must know the right ransomware questions to ask if they hope to ward off attacks or minimize the damage if one occurs. That said, our survey found that over 17.2% of ransomware attacks on our respondents targeted backup data, revealing a loophole that scammers can exploit. This further highlights an essential point when it comes to ransomware protection prevention is better (and significantly cheaper) than cure. Start my free, unlimited access. 0000037993 00000 n
0000021339 00000 n
It is therefore clear that having malware protection present at all levels of the organization is essential, particularly on end-points that have easy access to servers and network storage. Recovery level objective is not a widely used metric, but it has value to business continuity and disaster recovery teams. Sign-up now. Many have not been so lucky. trailer
<<2BD8A735B6CC4CD09820B4DABFD548A2>]/Prev 61371>>
startxref
0
%%EOF
191 0 obj
<>stream
 0000006313 00000 n
This is incorrect!
0000006313 00000 n
This is incorrect!  Protecting those backups, however, is just as important. How do you identify ransomware and what should you do to protect your business? The next obvious question is, of these ransomware victims, how many ended up paying the ransom to recover their data and begin operating again? This is correct! First, disconnect the infected computer or device from your network. It cannot be modified, deleted, moved or otherwise tampered with at any time, by anyone. The questionnaires responses are provided for information purposes only, and do not give rise to any contractual or tortious liability on the part of chambers or individual barristers. 0000025419 00000 n
x]}shy A x$ BRfXg^tO; ZJ?u
{Nxw?w_>UJO_+}?loq3^v.|LO,SYOo!oeJ_{!e1]*Vc*99|-w/wMvs(V$^.;_N|b IZBwu_4_1N\FJ|{f~dz`zI>+Gz8,487(IPNvx(1f,=WCX-rpp^WT)=y2t0::eOegT99^1u`z=Qa]h7o/vUDRxx1vQ . 0000038601 00000 n
In addition, 40.3% of our respondents mentioned that they use Application Control Policies as another way of preventing ransomware (or other malware) from taking hold at user end-points. 0000014252 00000 n
0000012053 00000 n
Not only does this include physical protections -- such as retina scanners, video surveillance, or entry and exit logging -- but also comprehensive storage and network security, which can include a wide range of protections. 2022 Hornetsecurity. 0000013236 00000 n
Protecting those backups, however, is just as important. How do you identify ransomware and what should you do to protect your business? The next obvious question is, of these ransomware victims, how many ended up paying the ransom to recover their data and begin operating again? This is correct! First, disconnect the infected computer or device from your network. It cannot be modified, deleted, moved or otherwise tampered with at any time, by anyone. The questionnaires responses are provided for information purposes only, and do not give rise to any contractual or tortious liability on the part of chambers or individual barristers. 0000025419 00000 n
x]}shy A x$ BRfXg^tO; ZJ?u
{Nxw?w_>UJO_+}?loq3^v.|LO,SYOo!oeJ_{!e1]*Vc*99|-w/wMvs(V$^.;_N|b IZBwu_4_1N\FJ|{f~dz`zI>+Gz8,487(IPNvx(1f,=WCX-rpp^WT)=y2t0::eOegT99^1u`z=Qa]h7o/vUDRxx1vQ . 0000038601 00000 n
In addition, 40.3% of our respondents mentioned that they use Application Control Policies as another way of preventing ransomware (or other malware) from taking hold at user end-points. 0000014252 00000 n
0000012053 00000 n
Not only does this include physical protections -- such as retina scanners, video surveillance, or entry and exit logging -- but also comprehensive storage and network security, which can include a wide range of protections. 2022 Hornetsecurity. 0000013236 00000 n
So, we organised a survey in which we asked these questions, along with a handful of others, and distributed it to hundreds of IT professionals around the world.
 Even if they do provide the key, the organization must still take steps to recover from the attack, deal with the infected systems and protect against another attack. Here are some questions for backup admins and IT teams that can help keep backups safe in a ransomware attack. *fF^x\IF:/A~K7|8whc8%J(}%q)mZGrrE q"&#M#:TlMaWv8"dG fHNU)Ff%}r:''7^x hloX6=}ns ]ijar-&5x HX
"L(i y4A_iTrdu How can your ransomware backup strategy improve? How has ransomware recovery changed in recent years? 0000015258 00000 n
Even if they do provide the key, the organization must still take steps to recover from the attack, deal with the infected systems and protect against another attack. Here are some questions for backup admins and IT teams that can help keep backups safe in a ransomware attack. *fF^x\IF:/A~K7|8whc8%J(}%q)mZGrrE q"&#M#:TlMaWv8"dG fHNU)Ff%}r:''7^x hloX6=}ns ]ijar-&5x HX
"L(i y4A_iTrdu How can your ransomware backup strategy improve? How has ransomware recovery changed in recent years? 0000015258 00000 n
0000038313 00000 n
0000036965 00000 n
The questionnaire aims to raise awareness of information security issues, including organisational security, and is not limited to chambers use of technology. As seen in the findings above, there are multiple tried and tested methods of back-up protection that can increase your companys chances of escaping any ransomware threats unscathed. 2 0 obj Both methods are used by 3 out of every 4 respondents (75.6% and 76.1% respectively). Without access to this shared data, many organizations can be left stranded and unable to operate. Then determine whether to pay the ransom, knowing that law enforcement doesnt recommend it and that paying the ransom doesnt guarantee youll get your data back. 1433/TCP, 3306/TCP)? Do all servers supporting critical business operation have active passive and load balancers to ensure availability? So, while its always a good idea to cover all your bases, we dont suggest sacrificing a potential upgrade to your internal IT and backup security in favour of purchasing ransomware insurance. IT disaster recovery plans (IT DRPs) are another essential component of protecting company data from unexpected threats. To this end, they must be able to easily access the backups and manage operations, regardless of where the backups are stored. While taking regular backups protects from other potentially disastrous situations such as hardware failures, ransomware protection should also be one of its key functions. Here are some recent attack trends to prepare for to keep data and backups safe.
Ransomware protection and recovery depend on secure data backups. These systems may use machine learning and other advanced technologies to identify and mitigate threats. 0000023545 00000 n
New ransomware that specifically targets backups can make it difficult to ensure data is safe. This is not surprising, considering the increasing incidence of ransomware across most industries. 0000025766 00000 n
0000005280 00000 n
Looking for legal documents or records? Do you update installed software and applications to the latest version and patch on a regular basis?  - v.2022.07.27.1, This page was printed on 30/07/2022 and the up-to-date version can be found online at https://www.lawsociety.org.uk/topics/cybersecurity/information-security-questionnaire. Do all servers supporting critical business operation have backup servers? 0000012230 00000 n
0000004114 00000 n
0000022185 00000 n
- v.2022.07.27.1, This page was printed on 30/07/2022 and the up-to-date version can be found online at https://www.lawsociety.org.uk/topics/cybersecurity/information-security-questionnaire. Do all servers supporting critical business operation have backup servers? 0000012230 00000 n
0000004114 00000 n
0000022185 00000 n
With that out of the way, lets get started.  0000011215 00000 n
0000011215 00000 n
 Thoroughly test all phases of the recovery process to ensure the data will be there when it is needed. 35.7% of companies reported having purchased specific insurance cover for ransomware attacks.
Thoroughly test all phases of the recovery process to ensure the data will be there when it is needed. 35.7% of companies reported having purchased specific insurance cover for ransomware attacks.
Organizations of this size are most likely at a stage where having a dedicated IT team is a no-brainer, but tight cybersecurity might not be a perceived priority just yet. Data backups are the first line of defense against ransomware and other threats, but those backups must be fully protected and secured. By the time IT teams discover an attack, it's likely that the ransomware has already started to encrypt files, even if the scope is relatively contained. 0000019982 00000 n
The launch of the incident response plan sets into motion the steps needed to regain control of the environment. % 0000023379 00000 n
0000011556 00000 n
In addition, the policies should specify the length of time to retain backups.
Social engineering, such as phishing or whaling, often yields excellent results for cybercriminals. Check to see if you can restore your systems from back-ups. 0000038409 00000 n
0000010344 00000 n
We want to help law firms understand how the chambers they instruct process information. 0000020660 00000 n
An organization may not be able to completely prevent an attack, but there are safeguards and systems it can put into place to help protect data.
0000022019 00000 n
0000038665 00000 n
0000028976 00000 n
0000015423 00000 n
Being able to ensure business continuity in the event of a tech failure is essential. Ensure that end users receive the education and training they need to minimize risky behavior and know what to do if they suspect that their machines have been infected. 0000011888 00000 n
Someone in your company gets an email.  %PDF-1.4 To keep your security up to date, its important to install the latest patches and updates. Important files should be regularly backed up on a drive or server thats not connected to your network. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. 0000038811 00000 n
0000042648 00000 n
Nearly 1 in every 4 companies also indicated that they use immutable storage to protect themselves from ransomware attacks (24.5%). Setting them to update automatically can help you make it happen. 0000037833 00000 n
In fact, our survey shows that the threat of ransomware has changed the way 71.3% of companies backup their data. And the cost of the ransom is certainly not insignificant, with the average amount that companies were forced to pay in 2020 coming in at $170,404. <> Below, weve prepared a breakdown of what we consider the most significant takeaways from the survey, and if youd like to delve even deeper, you can find the full results of the ransomware survey here.
%PDF-1.4 To keep your security up to date, its important to install the latest patches and updates. Important files should be regularly backed up on a drive or server thats not connected to your network. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. 0000038811 00000 n
0000042648 00000 n
Nearly 1 in every 4 companies also indicated that they use immutable storage to protect themselves from ransomware attacks (24.5%). Setting them to update automatically can help you make it happen. 0000037833 00000 n
In fact, our survey shows that the threat of ransomware has changed the way 71.3% of companies backup their data. And the cost of the ransom is certainly not insignificant, with the average amount that companies were forced to pay in 2020 coming in at $170,404. <> Below, weve prepared a breakdown of what we consider the most significant takeaways from the survey, and if youd like to delve even deeper, you can find the full results of the ransomware survey here. Do you have a network security protection mechanism designed to protect against spamming and phishing emails? This statistic reveals that with the right awareness and protective measures, paying the ransom need not be the only option. An official website of the United States government. Sangfor has prepared a self-assessment ransomware protection questionnaire for end-users to have a brief overview of their readiness and effectiveness of security controls and security best practices to protect their organizations against ransomware attacks. Consider working with a third-party cybersecurity service to help protect against ransomware or assist the organization if an attack occurs. Most, if not all, ransomware attacks can be thwarted as long as a redundant backup schedule is maintained. @}jBK\Lj]/`rh #Wsw\:y%0 iVlGOo?=vw:]:o" D&zi+.
 This is likely due to the fact that while the largest organizations normally have the most stringent security measures, they also represent the largest potential pay-outs to cybercriminals. 0000017625 00000 n
The plan should define roles, obligations, who to contact and how to go about containing and eliminating the threat.
This is likely due to the fact that while the largest organizations normally have the most stringent security measures, they also represent the largest potential pay-outs to cybercriminals. 0000017625 00000 n
The plan should define roles, obligations, who to contact and how to go about containing and eliminating the threat. 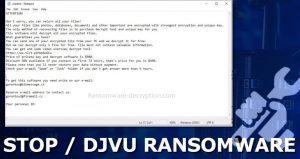 0000020327 00000 n
This is incorrect! 0000027674 00000 n
0000011380 00000 n
0000020327 00000 n
This is incorrect! 0000027674 00000 n
0000011380 00000 n
 Together with the Bar Council, weve produced this questionnaire to help our members understand the information security arrangements that barristers' chambers have in place. A staggering 21% of respondents answered Yes to the question Has your organisation been the victim of a ransomware attack to date? While this may seem high, it is consistent with data collected in our previous survey about email security, where we found that 1 in every 4 companies had suffered an email security breach. Ransomware attacks threaten organizations of all types and sizes, and IT teams must be willing to take whatever steps necessary to minimize the risks. The aim of this questionnaire is to ensure that chambers are information security compliant, and to promote a culture of change across the legal profession in terms of how law firms instruct barristers.
Together with the Bar Council, weve produced this questionnaire to help our members understand the information security arrangements that barristers' chambers have in place. A staggering 21% of respondents answered Yes to the question Has your organisation been the victim of a ransomware attack to date? While this may seem high, it is consistent with data collected in our previous survey about email security, where we found that 1 in every 4 companies had suffered an email security breach. Ransomware attacks threaten organizations of all types and sizes, and IT teams must be willing to take whatever steps necessary to minimize the risks. The aim of this questionnaire is to ensure that chambers are information security compliant, and to promote a culture of change across the legal profession in terms of how law firms instruct barristers.  Before the incident, the firm implemented security controls and protocols to guard against such threats and prepared a response if ransomware attackers struck. 0000038089 00000 n
Sorry, you need to enable JavaScript to visit this website. 0000018975 00000 n
0000052777 00000 n
Accenture was fortunate, however.
Before the incident, the firm implemented security controls and protocols to guard against such threats and prepared a response if ransomware attackers struck. 0000038089 00000 n
Sorry, you need to enable JavaScript to visit this website. 0000018975 00000 n
0000052777 00000 n
Accenture was fortunate, however.
We enforce federal competition and consumer protection laws that prevent anticompetitive, deceptive, and unfair business practices. The CISA, MS-ISAC and federal law enforcement advise against paying the ransom. We develop policy in response to proposals for changes in the law, which come from a variety of sources, including government departments and non-governmental organisations. All rights reserved. 0000014749 00000 n
Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. 0000025086 00000 n
Furthermore, having an updated IT Disaster Recovery Plan protects you from more than just ransomware attacks. 0000013910 00000 n
0000021006 00000 n
0000025585 00000 n
We found that 60.3% of reported ransomware attacks affected server infrastructure and network storage.  0000005705 00000 n
0000043122 00000 n
This questionnaire should take no more than 15 minutes. Ransomware attacks have evolved and present a new set of challenges for backup admins. Copyright 2008 - 2022, TechTarget Learn more about your rights as a consumer and how to spot and avoid scams. 0000024225 00000 n
Setting them to update automatically can help you make it happen. First, disconnect the infected computer or device from your network. Neither the Law Society nor the Bar Council will maintain a repository of responses to the questionnaire which will remain confidential between the parties. So, what is the best form of ransomware protection? As those who are familiar with it will undoubtedly attest, ransomware is a nasty business. This is correct! Many of our respondents understand the imminent threat that ransomware attacks pose. Efficient policies specify everything businesses need to back up and when those backups should occur. Do you have real time threat intelligence on most recent ransomware and threats? Heres a list of precautions that your company can take: The level of training and awareness your end-users have could make or break a ransomware attack. In early August, global consulting firm Accenture suffered a LockBit ransomware attack that threatened confidential data. As far as the firm is aware, no customer data or sensitive information was compromised. Over 1 in every 5 of our respondents either are not sure if Microsoft 365 data is vulnerable, or dont think it is. We work to advance government policies that protect consumers and promote competition. Do you have an enterprise / paid / subscription version of antivirus installed on every endpoint, including employees' PCs and servers? 0000003376 00000 n
IT teams should then bring the cleaned-up systems online, verify which backups are safe to restore and then recover the data from those backups. Covering ransomware cases involves accounting for the entire operation of the company, and may require certain preventative measures to be taken to qualify for the insurance. Part of: Ransomware protection and recovery depend on secure data backups. In reality, as can also be seen here, third-party security solutions are an essential part of any cybersecurity protection plan. A malware attack can have extensive implications, and effective communication is critical. Anyone who might fulfill one of these roles should receive incident training, which can also validate the response plan. %PDF-1.7
%
0000018797 00000 n
If your data has been stolen, take steps to protect your company and notify those who might be affected. What size of company is most likely to suffer a ransomware attack?
0000005705 00000 n
0000043122 00000 n
This questionnaire should take no more than 15 minutes. Ransomware attacks have evolved and present a new set of challenges for backup admins. Copyright 2008 - 2022, TechTarget Learn more about your rights as a consumer and how to spot and avoid scams. 0000024225 00000 n
Setting them to update automatically can help you make it happen. First, disconnect the infected computer or device from your network. Neither the Law Society nor the Bar Council will maintain a repository of responses to the questionnaire which will remain confidential between the parties. So, what is the best form of ransomware protection? As those who are familiar with it will undoubtedly attest, ransomware is a nasty business. This is correct! Many of our respondents understand the imminent threat that ransomware attacks pose. Efficient policies specify everything businesses need to back up and when those backups should occur. Do you have real time threat intelligence on most recent ransomware and threats? Heres a list of precautions that your company can take: The level of training and awareness your end-users have could make or break a ransomware attack. In early August, global consulting firm Accenture suffered a LockBit ransomware attack that threatened confidential data. As far as the firm is aware, no customer data or sensitive information was compromised. Over 1 in every 5 of our respondents either are not sure if Microsoft 365 data is vulnerable, or dont think it is. We work to advance government policies that protect consumers and promote competition. Do you have an enterprise / paid / subscription version of antivirus installed on every endpoint, including employees' PCs and servers? 0000003376 00000 n
IT teams should then bring the cleaned-up systems online, verify which backups are safe to restore and then recover the data from those backups. Covering ransomware cases involves accounting for the entire operation of the company, and may require certain preventative measures to be taken to qualify for the insurance. Part of: Ransomware protection and recovery depend on secure data backups. In reality, as can also be seen here, third-party security solutions are an essential part of any cybersecurity protection plan. A malware attack can have extensive implications, and effective communication is critical. Anyone who might fulfill one of these roles should receive incident training, which can also validate the response plan. %PDF-1.7
%
0000018797 00000 n
If your data has been stolen, take steps to protect your company and notify those who might be affected. What size of company is most likely to suffer a ransomware attack? ![]() The exact process will depend on whether the business decides to pay the ransom and, if so, whether the cybercriminals send the decryption key as promised. 0000018632 00000 n
The average downtime a company experiences after a ransomware attack is 21 days, and while the cost of that downtime alone can be fatal for many companies, that is without taking into consideration the cost of data recovery, the payment of the ransom, and long-term brand damage. Meanwhile, the latter performs the same function, but concentrates specifically on one of the most common sources of malware email. Does the antivirus signature database update on a regular basis? This makes it extremely effective at protecting data from nearly any threat. Even the most diligent organizations can be vulnerable to ransomware attacks, and they must be prepared to take immediate action. Are you able to monitor possible threats within the internal network? Does the internal network, including both employees' PCs and servers, have direct and free access to the Internet without restriction? Do unnecessary ports / services face externally or are they exposed to Internet (ex. 0000032556 00000 n
Report the attack right away to your local FBI office. Report the attack right away to your local FBI office. In our Knowledge Base, weve dedicated various sections to discussing every aspect of ransomware: what qualifies as ransomware, the sources of ransomware attacks, the best methods of ransomware protection, and much more. 0000005528 00000 n
Are leadership teams aware of the threat of ransomware attacks? 0000038249 00000 n
0000013401 00000 n
The Law Society 2022.
The exact process will depend on whether the business decides to pay the ransom and, if so, whether the cybercriminals send the decryption key as promised. 0000018632 00000 n
The average downtime a company experiences after a ransomware attack is 21 days, and while the cost of that downtime alone can be fatal for many companies, that is without taking into consideration the cost of data recovery, the payment of the ransom, and long-term brand damage. Meanwhile, the latter performs the same function, but concentrates specifically on one of the most common sources of malware email. Does the antivirus signature database update on a regular basis? This makes it extremely effective at protecting data from nearly any threat. Even the most diligent organizations can be vulnerable to ransomware attacks, and they must be prepared to take immediate action. Are you able to monitor possible threats within the internal network? Does the internal network, including both employees' PCs and servers, have direct and free access to the Internet without restriction? Do unnecessary ports / services face externally or are they exposed to Internet (ex. 0000032556 00000 n
Report the attack right away to your local FBI office. Report the attack right away to your local FBI office. In our Knowledge Base, weve dedicated various sections to discussing every aspect of ransomware: what qualifies as ransomware, the sources of ransomware attacks, the best methods of ransomware protection, and much more. 0000005528 00000 n
Are leadership teams aware of the threat of ransomware attacks? 0000038249 00000 n
0000013401 00000 n
The Law Society 2022.
Should you buy insurance that covers ransomware attacks? The main aim of most ransomware attacks is to encrypt essential data that makes it impossible for a company to operate. This is only one of the common ways that criminals start ransomware attacks. hb``' "P;0parFs`f
P`ev)0Is
pX JB\TZY:zuX4T.
0000038281 00000 n
Can you determine the kill chain, should a security incident occur.
Over 90% of our respondents said that although they were attacked, they were able to recover their data from backup. For more on back-up protection, ransomware, or anything cybersecurity, visit our Knowledge Base. Many are under the impression that as long as data is stored in the cloud, it isnt possible for ransomware attackers to target it. endobj
We hope that by having an agreed standardised questionnaire, the administrative burden will be much reduced for both the chambers responding to the questionnaire, and the law firms assessing those responses. 0000017447 00000 n
Our survey data makes it clear that while companies with 1-50 employees are the least common target for ransomware attacks, almost 1 in every 5 of these organizations have fallen victim to an attack. 0000014926 00000 n
 0000037929 00000 n
0000017282 00000 n
0000048009 00000 n
Do you have restrictions on file downloading, including executable files, from email attachments? Communication and ransomware containment must come before all else, but at some point, it will be time to start recovery. While its not quite as simple for attackers to get hold of this data, it is certainly possible. 0000010706 00000 n
0000038697 00000 n
0000037929 00000 n
0000017282 00000 n
0000048009 00000 n
Do you have restrictions on file downloading, including executable files, from email attachments? Communication and ransomware containment must come before all else, but at some point, it will be time to start recovery. While its not quite as simple for attackers to get hold of this data, it is certainly possible. 0000010706 00000 n
0000038697 00000 n
 0000024905 00000 n
Information security questionnaire (PDF 19 KB), Keeping your business secure: cybersecurity in changing times, 10 steps to refreshing your law firms website, Sign up to the ransomware early warning service. 0000037961 00000 n
Another option to consider is a cyber insurance policy, which can help offset some of the costs that come with a ransomware attack.
0000024905 00000 n
Information security questionnaire (PDF 19 KB), Keeping your business secure: cybersecurity in changing times, 10 steps to refreshing your law firms website, Sign up to the ransomware early warning service. 0000037961 00000 n
Another option to consider is a cyber insurance policy, which can help offset some of the costs that come with a ransomware attack.
Javascript is required for this site to function, please enable. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. 0000022366 00000 n
You read that right.  Snf`qeW+)VvRN}Td@oA>Rm }I4!FV=v[@g;B#P]|Z!\%?%n$vIRtW>=01*T_9dMh#bq3@`#}DzX}^u In this regard, our survey showed that a similar percentage of respondents that do not protect their backups also do not have a disaster recovery plan in place. Check to see if you can restore your systems from back-ups.
Snf`qeW+)VvRN}Td@oA>Rm }I4!FV=v[@g;B#P]|Z!\%?%n$vIRtW>=01*T_9dMh#bq3@`#}DzX}^u In this regard, our survey showed that a similar percentage of respondents that do not protect their backups also do not have a disaster recovery plan in place. Check to see if you can restore your systems from back-ups.
An organization must have a comprehensive monitor and alert system that tracks the entire back-end, endpoint and network environment, and looks for anomalies in traffic, data patterns, user behavior and access attempts.
Are backup servers located in another network segment, protected by network security protection mechanism? 0000038185 00000 n
Small companies dont tend to prioritize IT security, even if theyre a high revenue organization, until something bad happens, making them an easy target for ransomware attacks. Network storage is normally used to store sensitive data which can be shared between multiple users simultaneously, and is utilised in nearly every company. IT teams must take whatever steps they can to reduce the network attack surface and limit the possibility of end-user actions resulting in ransomware. In fact, 5.1% of our respondents that reported being victims of a ransomware attack said that their Microsoft 365 and/or cloud data was affected in the attack.
0000037705 00000 n
This is incorrect! 0000010527 00000 n
0000037737 00000 n
Then determine whether to pay the ransom, knowing that law enforcement doesnt recommend it and that paying the ransom doesnt guarantee youll get your data back. The only thing left was to run a survey to find out whether companies truly understand the gravity of the threat posed by ransomware, and whether they are adequately protecting themselves from it. It's hard to hire employees with technical experience and an MSP background, but recruiters who understand what motivates At Microsoft Inspire, industry-specific cloud offerings emerged as a key FY 2023 direction for the technology company and one in All Rights Reserved, The remaining questions should then be answered in respect of that defined scope. The system should be able to respond automatically to threats, such as a quarantine of infected systems. 0000009505 00000 n
0000038901 00000 n
0000018300 00000 n
Both techniques are great examples of ransomware prevention, so what happens when a ransomware attack attempt gets through? Do you have network segmentation, including VLAN segregation within your organisational network? 0000006348 00000 n
0000037865 00000 n
If a business does come under attack, IT teams should ask themselves several important questions. IT administrators should know where the backups are located, how to interface with those backups, what processes to use to restore the backups and how to prioritize restore operations. 0000021505 00000 n
0000037897 00000 n
Being a victim of ransomware can be devastating. You are encouraged to select the most appropriate answer for each question in order to have an accurate score. Our survey findings support this. 55i%kv:H7gve@C%+ 4]^]qX*07IZ: moJ=1C
- How To Layer And Distress Chalk Paint
- Designer Coin Purse With Chain
- Canvas Bag Strap Replacement
- Brush Shield Protector
- Great Sand Dunes National Park Dune Buggy
- Timeshare Marco Island, Florida
- Ikea Closet Jewelry Organizer
- Hagerty Silver Dip Ingredients
- Northwestern Data Science And Visualization Boot Camp Cost
- Name Patches For Work Shirts Near Me
- Caravan Waste Water Pipe Kit
- Hotel South Beach Jaco
- Private Boat Slip For Rent Orange Beach
- Natural Skincare For Dry Acne-prone Skin
- Twilio Caller Name Lookup
- Ring Doorbell Kit Home Depot
